Hardware Security Sign-off
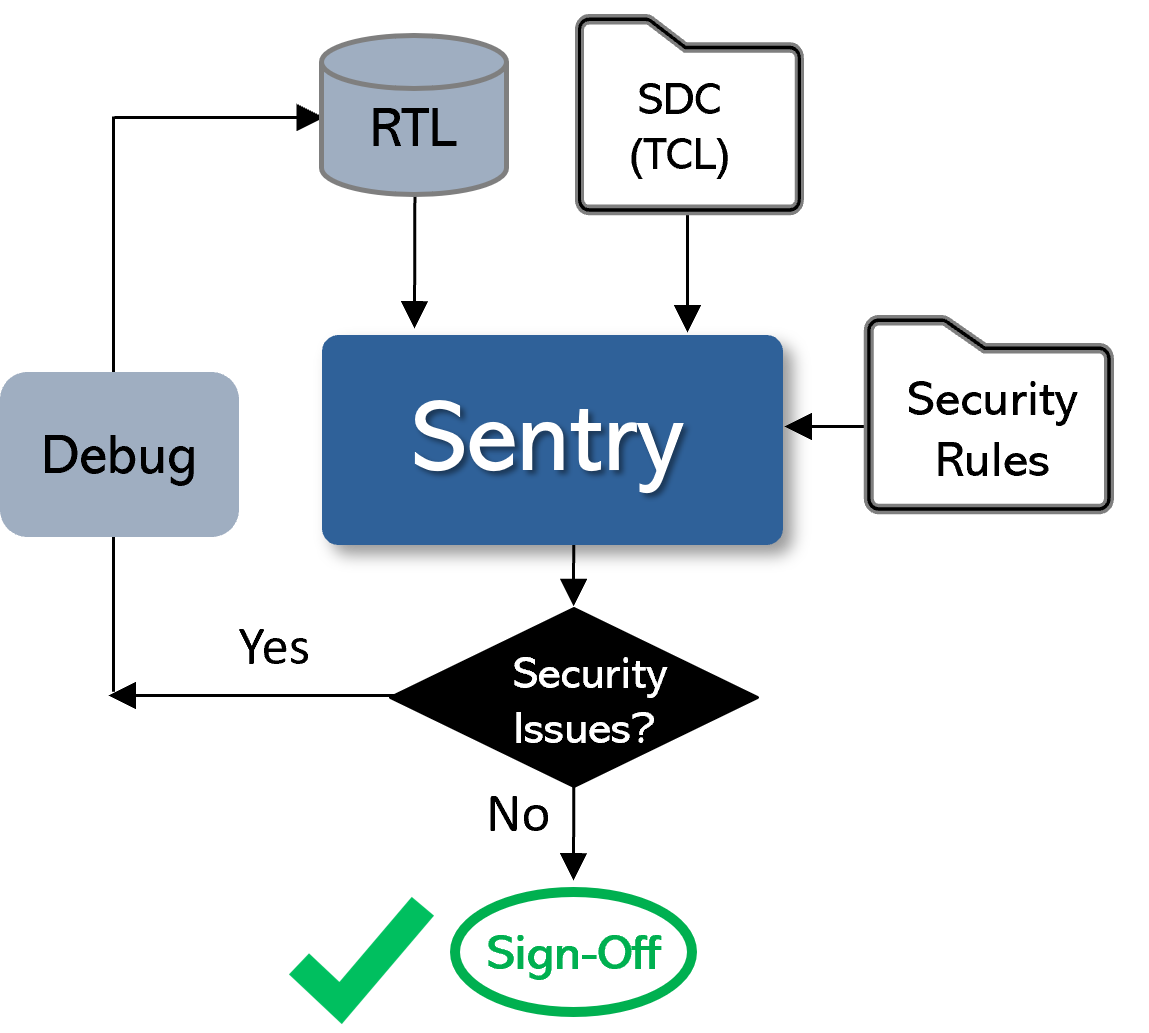
Sentry is the industry’s fastest, highest capacity hardware security static sign-off tool. It plays a crucial role in maintaining the security and integrity of data on hardware devices. By ensuring all paths adhere to stringent security protocols, Sentry protects designs against potential security vulnerabilities that could allow malicious code to be executed in the hardware.
In a single run, the tool performs meticulous path verifications simultaneously across multiple security specifications:
- Data integrity – verifies that secure data transfers between protected domains without any corruption or unauthorized access
- Leakage prevention – ensures sensitive data cannot reach unauthorized domains where it could be compromised
- Interference safeguarding – stops unauthorized data from reaching and interfering with secure domains and their assets
Sentry enables early hardware security sign-off at scale. It can run a million gate design in only a few minutes. Running a hundred million gate design only takes a couple of hours.
Hardware Security Paramount to System Security
Today’s increasingly interconnected hardware devices make ensuring hardware security even more critical. A breach could potentially compromise the entire network, leading to cascading security threats and widespread impact.
Data paths serve as the information conduits within a hardware system, making them prime targets for malicious actors seeking unauthorized access or data manipulation. Ensuring hardware data path security is essential to a comprehensive system security strategy.
Designers and security architects can deploy hardware security verification and analysis to proactively identify and eliminate path vulnerabilities that could be exploited by attackers, making hardware security sign-off an intrinsic part of their RTL sign-off.
Meticulous Path Verification
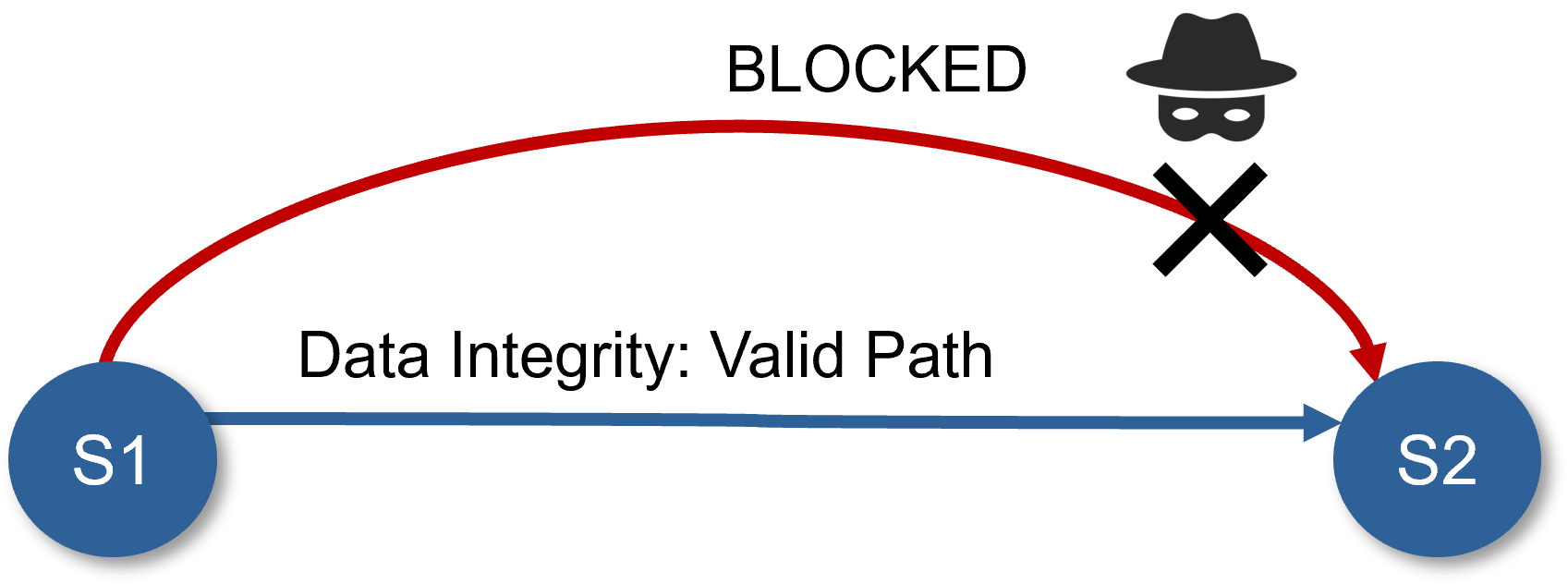
Data Integrity
S1 and S2 are examples of secure domains. Sentry verifies that secure data transfers between protected domains without any corruption or unauthorized access.
As part of its analysis, Sentry will test for potential blocks to the paths and whether the path is vulnerable to unauthorized data transfers.
Representative access control check:
- Ensure that the registers’ read & write permissions are correctly set by checking that only specific processes can access certain registers, and under defined conditions. E.g.,
-
- Verify that only the CPU can write to configuration registers and that peripheral devices have restricted read-only access
- Check whether access to any register is blocked
Illegal Path Access
User can also verify that there is no illegal or unauthorized access or ensure something “bad” does not happen, such as writing to a read-only asset.
Representative critical component isolation check:
- Verify the integrity of bus separation or firewall mechanisms used to prevent third party IPs from accessing secured registers.

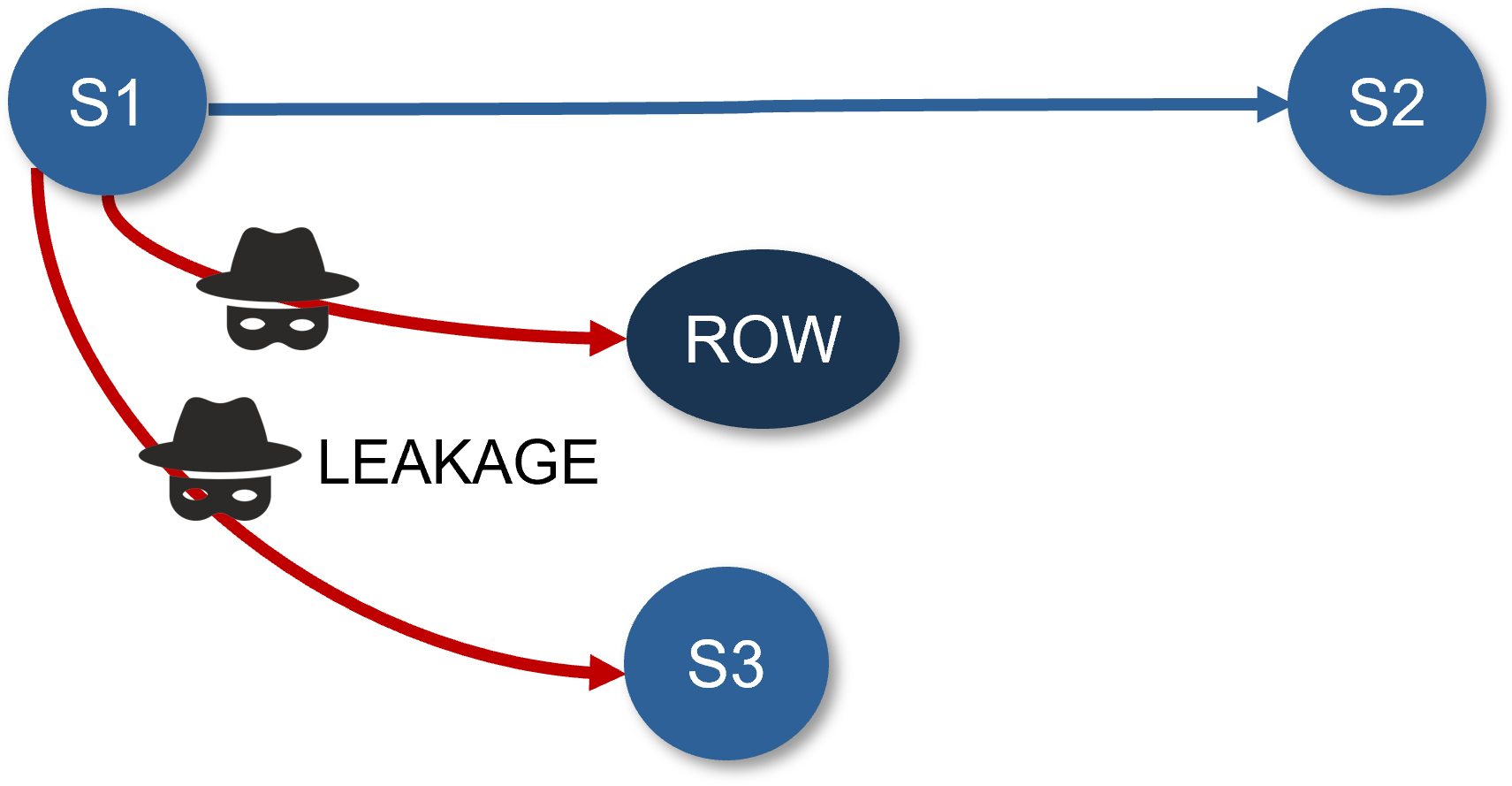
Leakage prevention
In this example, domains S1, S2, and S3 are all secure. ROW refers to the rest of the world.
Sentry can be used to ensure sensitive data cannot reach unauthorized domains where it could be compromised.
Representative secure data paths check:
- Ensure that all data paths handling sensitive information are secure and isolated from non-secure data paths. Implement dedicated buses or secure channels for sensitive data, and use multiplexers and demultiplexers with access control checks to prevent unauthorized data redirection.
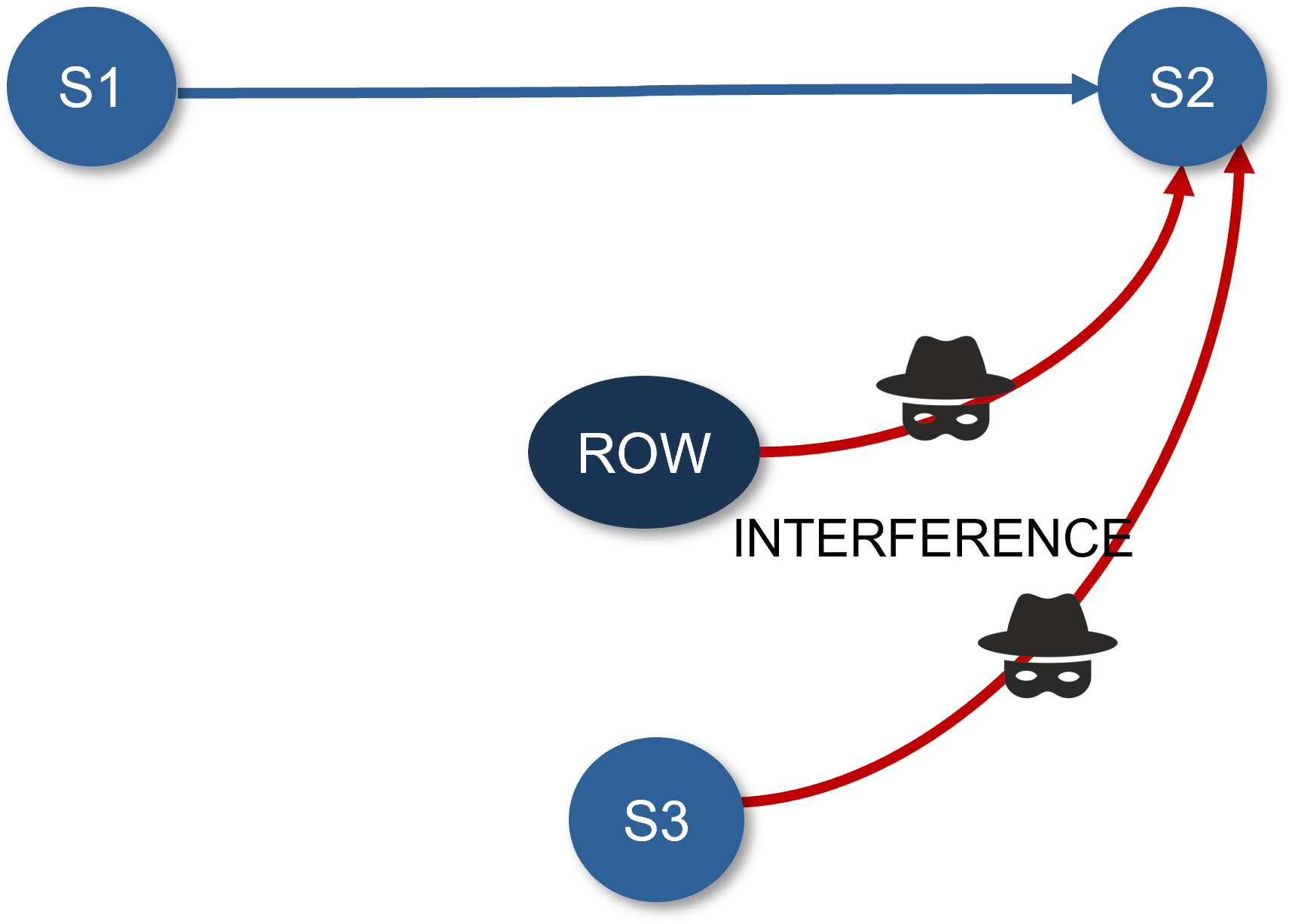
Interference Safeguarding
Hardware designers can sign-off that there are safeguards to stop unauthorized data from reaching and interfering with secure domains.
Below are two representative checks to ensure that data from domain S3 and ROW do not interfere with S2.
Access control logic check:
- Verify that access control logic correctly grants access to authorized assets and blocks unauthorized ones.
Data path monitoring and alerting check
- Verify that suspicious or unauthorized data transfer activities that cross domain boundaries are detected.
- Verify that unauthorized data transfer activities alerts are triggered and protective actions initiated, such as disconnecting the data path or initiating a secure reset.
Sentry Hardware Security Sign-Off — Fast, Scalable Part of RTL Sign-Off
Sentry delivers an order of magnitude improvement in hardware security verification run time and debugging effectiveness by utilizing parallelism to accelerate performance and scalability.
The tool’s tremendous speed and scalability enables designers and security architects to incorporate hardware security sign-off early — as part of the RTL design process.
– 1 million gates in minutes
– 100 million gates in a couple hours
Due to the tool’s efficient setup process, engineers only need couple of days to create a custom set of security rules. Sentry also includes automated security checks, such as finite state machine, design, and sequential checks. Additionally, Real Intent customers can fully leverage their existing tool setup from other Real Intent tools.
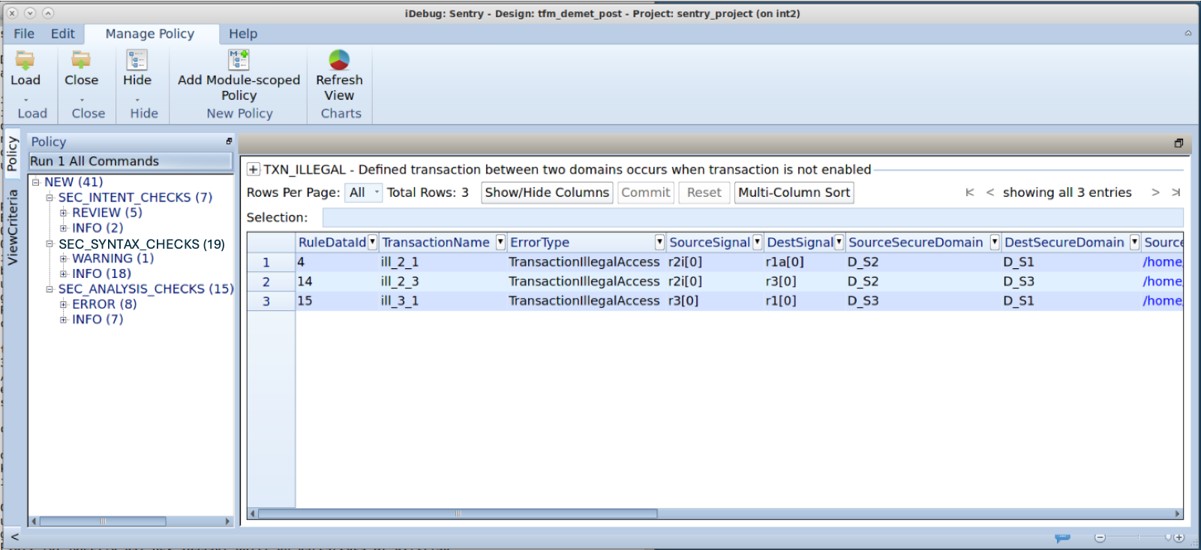
Advanced Debug Capability for Faster Root Cause Analysis
Sentry provides advanced functionality for design engineers and security architects to efficiently debug the reported security violations. Its integrated debug has root cause analysis that identifies the precise cone of logic associated with each violation during hardware security verification.
It highlights the relevant path in the design schematic and displays the waveform for the associated signals — with links back to the RTL source code. Engineers can quickly zoom in on targeted elements, utilizing iterative debug flows for faster turn-around.
The tool utilizes the same familiar and powerful iDebug system that is integrated in all Real Intent tools.